Pluck w00t!
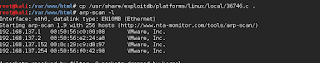
Time to Pluck! Though a bit late, I decided to give this machine a try! As with all almost every machine I began with arp-scan/netdiscover: Once this is done, next I try to do a port scan on the host. I began with the tcp scan while upd scans taking more time ran in the background. Since port 80 was open, I ran nikto in other window. Post this is done, I move next to check banners on each service. SSH dint give any banner, neither mysql or llmnr protocol so I tried to enumerate the web. Just before I went to check the web service, I looked at the nikto results and they were interesting! Now, this was very interesting, an LFI!! Meanwhile I had also tried fuzzing the admin page on the webservice and it revealed sql injection: Now, I had two vectors so I thought lets begin with the LFI. Doing a /etc/passwd dumped all the contents!! But Trying lfi on other files like apache logs etc was not getting possible (permission issue??) This was when som